Data Privacy & System Security
Overview
Information Security and Data Privacy is the #1 prerequisite for any Huski.ai SaaS offering. Through the years, we have gone above and beyond to implement the following security architecture based on the industry standard principles of information security and data privacy, including but not limited to separation of duty, role based access control, data governance, and privacy-aware computing.
The following chart gives an overview of how these principles are implemented and how our system is secured. Let’s dive into details in the rest of the article.
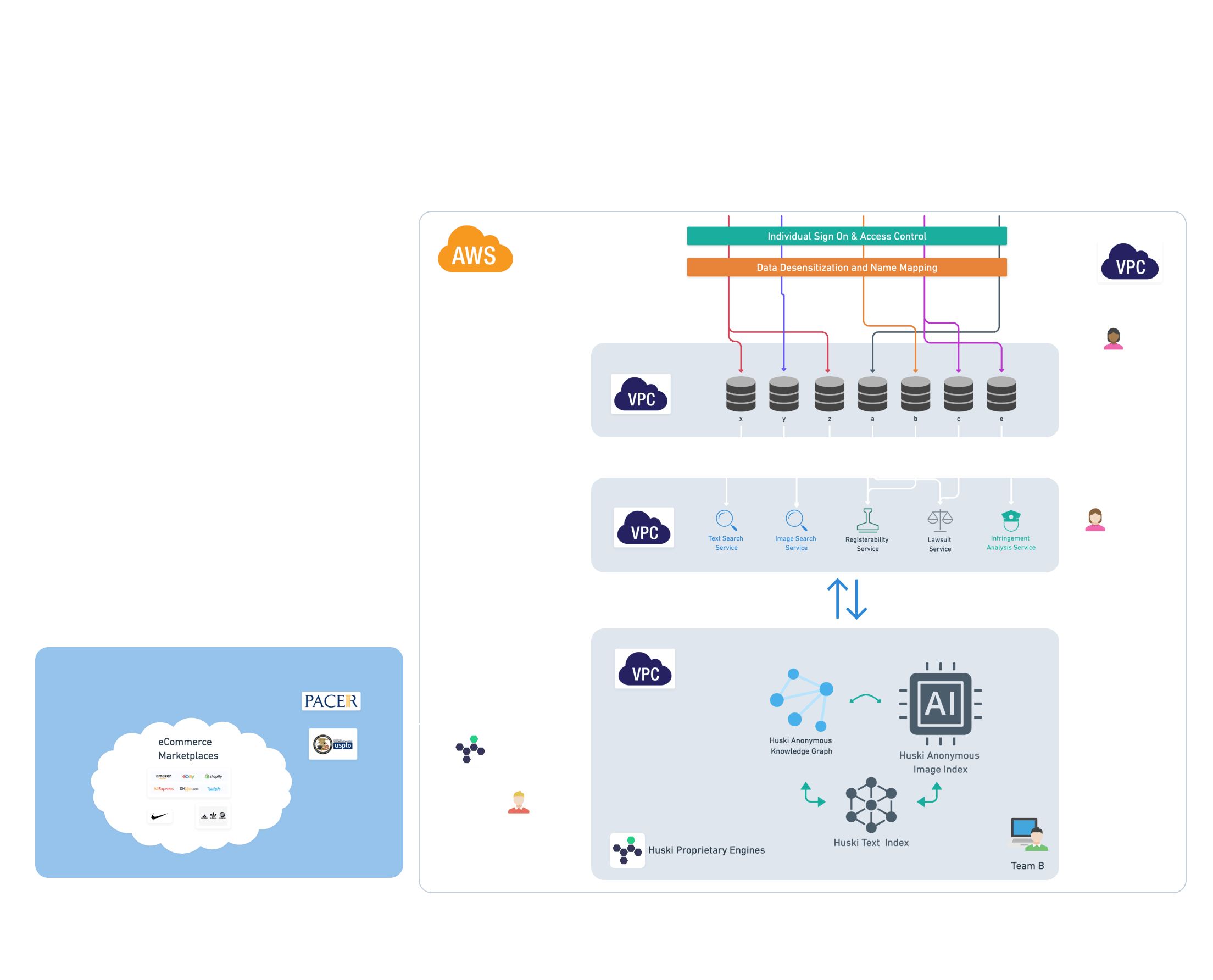
System Security
Huski AI’s SaaS solutions are implemented on the AWS (Amazon Web Services) platform. AWS is a leading cloud provider which offers a range of functions, such as databases, elastic computing resources, content delivery and management systems, and microservice building blocks.
AWS puts security at the top of its priority list. The entire AWS offering is built to meet modern security requirements and it has been adopted by the most security-sensitive organizations such as Dow Jones, NASA, and US Department of State. AWS is also constantly evolving the security features such as identity management and access control, logging and monitoring, key management and encryption, networking intrusion detection, and Distributed Denial of Service (DDoS) protection.
Huski AI leverages AWS and implements the following security measures to ensure we have a reliable system against hacking and outside attacks.
- Two Factor Authentication for developers to login to the development environment. This is to reduce the risk of impersonate attacks, or man-in-the-middle attacks.
- Firewalls among local and remote networks as well as https connections. This is to encrypt traffic to ensure data privacy and security.
- Microservice architecture and throttling thresholds. This is to ensure the overall system is very hard to compromise, and avoid the DDoS attacks.
- Centralized Log Management and Analysis Engine. This is to discover security breaches and vulnerabilities at the earliest and guide our actions to eliminate threats.
- Role-based access control and separation of duty. This is to make sure the data and system is hard to be compromised, and even inside threats from potentially malicious personal.
- Regular data backup and redundancy of our database cluster. This is to make sure we have a reliable offering and disaster recovery mechanism.
- Key management and peripheral computing resources to reduce the risk of OS level zero day attacks.
- Modern Continuous Integration and Continuous Deployment (CI/CD) procedure to make sure the separation of the production environment from staging and developing environments.
Data Security
Building, insights data which are derived from raw data with our AI algorithms, and the user activity data.
We adopted AWS Simple Storage Service (S3) and Aurora database, AWS Lambda, AWS Batch, and AWS EC2 and ECS (elastic computing and elastic cluster service) to do the raw data collection, cleaning, and insight driven discovery and development. The data redundancy and disaster recovery are built in with the above functions.
Our user historic activity data is stored in AWS Redshift cluster with AWS regions, availability zones, and secured connections throughout the whole internal data pipeline. The data is never touched by developers’ personal or company-provided computers and will stay in the same AWS region to compliant with certain privacy regulations, such as GDPR.
User Privacy
The Personal Identifiable Information (PII) is never accessed by the developers nor it is transferred outside of Huski AI’s AWS to any 3rd party. The PII is also separated from user activity history on www.huski.ai website before we do aggregated user behavior studies.
We also comply with GDPR to give our users full control of their activity data or personal information. Upon requests, we will delete all the activity trace from the users.
Our user terms and conditions can be found here.
Information security in software development procedure
Last but not least, we separate the developers into groups with independent access to their scopes of work only. We have a global team located in US and China. With the global presence of the company in the future, we may have additional team members in Europe or other places of the world. The AWS functionalities and the data they have access to are limited to their geolocation and their job functions.
Conclusion
Security and privacy are very active fields and the best practices may keep changing. Huski AI will be dedicated to make sure to keep up with the most recent advancements in the fields and provide a safe and reliable service to all of our users globally.
For questions or feedback, please reach out to us at contact@huski.ai.